The /etc/shadow file, also known as the shadow password file, is a Linux system file. Only the root user and shadow group members can access this file to prevent unauthorized access, and thus keep your system safe.
In this tutorial, we will learn about the shadow file and its format in detail.
What is /etc/shadow
/etc/shadow is a text file that stores encrypted passwords, along with user name, password expiration values, and last password change date. The credential information in the shadow file is encrypted using a one-way hash function to disable decryption.
When a user logs into the Linux system, the password in the /etc/passwd file is compared with the encrypted password in /etc/shadow after rehashing the password using a key. If these passwords do not match, the user is denied access.
The /etc/shadow password file enables enhanced authentication mechanisms by limiting access to the root user. A malicious user must know the hashing algorithm and the hash string to decrypt a password. After that, the malicious user will have to brute-force every password using different combinations and hash it to make sure it matches with the data stored in the shadow file.
What is the Use of /etc/shadow File
The shadow file is used by the Linux operating system to securely store user’s encrypted passwords. It provides the highest level of security against password cracking tools.
Passwords are an important part of the Linux operating system security. They are stored in the /etc/passwd file after encrypting using a randomly generated encryption key, which is also stored with the password. The encrypted passwords in the /etc/passwd file are denoted with an x. The passwd file is world-readable and unauthorized users can see these encrypted passwords using password cracking tools.
To address this security concern, Linux administrators can use the /etc/shadow password file. This file is readable only by the root user.
Shadow File Format
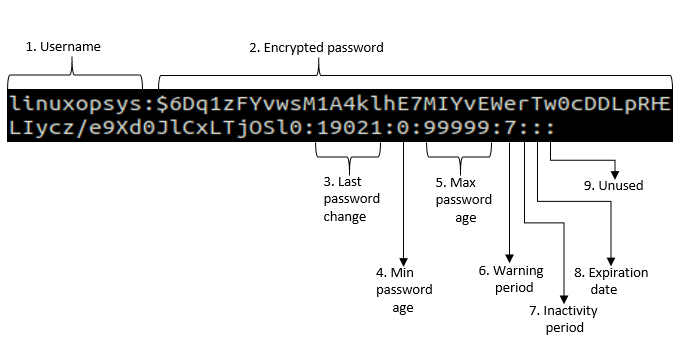
The shadow file has a total of 9 password fields that store different password information. The following figure describes the format of the shadow file:
You can check the password properties of a user using the chage command:
chage -l linuxopsys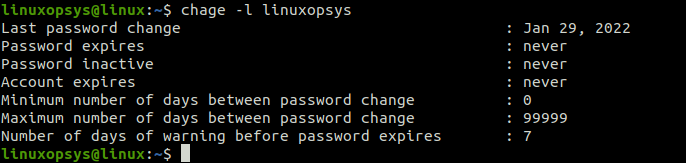
Fields in Shadow File
The shadow file contains user login name, user’s encrypted password, password expiration date, account expiration date, minimum and maximum password age, and other related details. This file has one entry per line and each line corresponds to one user listed in the /etc/passwd file. The first entry describes the root user, followed by other service and user accounts.
Every /etc/shadow entry has nine fields, which are separated by colons:
1. Username: User account name that exists in your system.
2. Encrypted password: User’s encrypted password. Password field is in the $type$salt$hashed format. The password hashes are part of the encrypted password value.
! in passwo! in the password field indicates that the user will not be able to login to the system using password authentication. In cases where a new user is created with a blank password, you may see this.
* implies that it is service account and user login is disabled but will be able to login by other means.
3. Last password change: Last password change date. The number of days are counted since 1st January, 1970.
4. Minimum password age: Minimum number of days after which the password can be changed. It is usually set to 0, which means the password can be changed immediately.
5. Maximum password age: Maximum number of days after which the password must be changed. It is set to 99999 by default.
6. Warning period: Number of days before password expires, during which a user is warned that the password needs to be changed.
7. Inactivity period: Number of days before the account is disabled after the user password expires.
8. Expiration date: Date on which the user account was disabled.
9. Unused: Empty field that is reserved for future use.
How to Access and Edit the Shadow File
You can access the shadow file using the cat command:
sudo cat /etc/shadow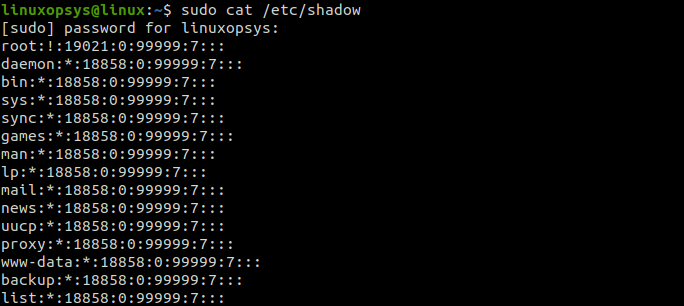
You can edit the shadow file using the vipw command:
sudo vipw -s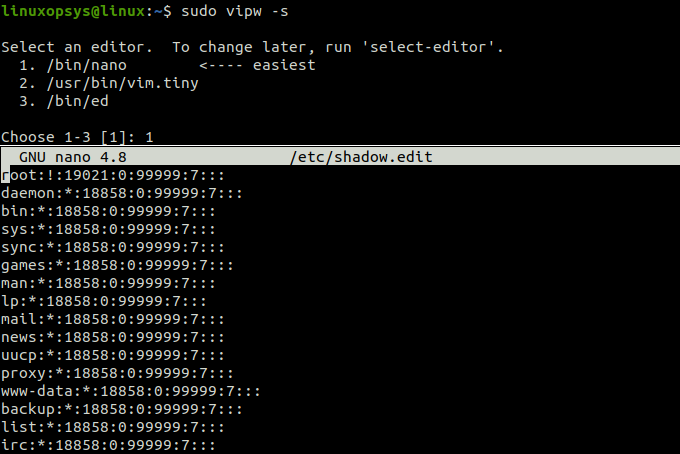
To avoid any security threats and system issues, it is not advised to edit the shadow file directly. If you need to change a password field in /etc/shadow, you can use the chage command.
For example, to set account expiration date, type:
sudo chage -E 2025-12-31 tomDifference between the /etc/passwd and /etc/shadow Files
- The /etc/passwd file contains user name, and user’s public information, such as full name, shell UID, and home directory. The shadow file contains encrypted password and password expiry information.
- The /etc/passwd file is world readable because applications use it to verify ownership and authentication. Whereas, the /etc/shadow password file is owned by the root user and the passwords in this file are hash encrypted.
- The /etc/passwd file supports only the basic Data Encryption Standard (DES) algorithms. However, /etc/shadow contents are encrypted using more advanced and complex encryption techniques.
Conclusion
In this tutorial, we learned about the shadow file, its format, and its contents. The shadow file contains encrypted user passwords with other password information. If you need to change a user’s password, you must use the passwd command, instead of editing the shadow file directly.



Comments