UFW (Uncomplicated Firewall) is the default tool in Linux for managing firewall rules. UFW logging enables users to read iptables containing the details about incoming or outgoing packets, their source and destination information, protocols for transmission, etc.
In this tutorial, we go through in-depth information about UFW logging.
Enable ufw logging
By default, ufw logging is disabled on Linux. The status of logs can be checked by running the below command:
sudo ufw status verbose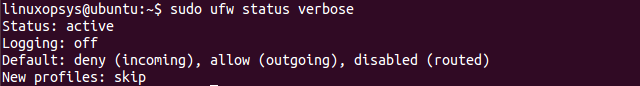
As we can see in the above image, the output returned contains whether or not the logging has been enabled. UFW logging can be enabled with the command:
sudo ufw logging onThis will enable logging with the default low log level as can be confirmed by running ufw with status verbose option as shown below:
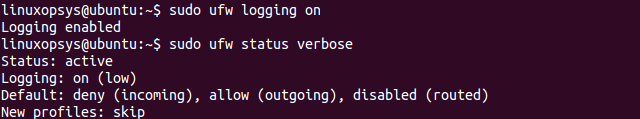
To disable UFW logging, we can simply pass the parameter as off:
sudo ufw logging offUFW log location
All logs, including UFW log on Linux filesystems are generally stored at the directory /var/log/. We can use ls command to list all the log files which are created by ufw:
sudo ls /var/log/ufw*Note: rsyslog should be enabled on the system for ufw log to work. The status of rsyslog can be check using the command:
sudo service rsyslog status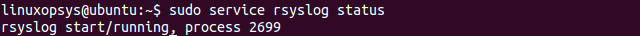
As we can see in the output above, the status of rsyslog is currently active (running)
How to view ufw log
We can use less command to check the log statements one page (screen) at a time using the below syntax:
sudo less /var/log/ufw*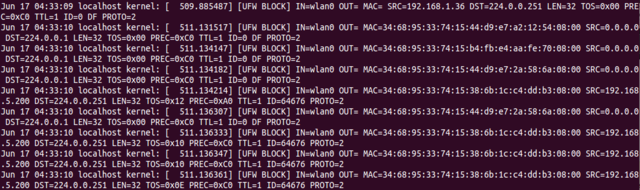
We can also use tail command to read the trailing log statements as they are logged into the ufw log file.
sudo tail -f /var/log/ufw.log
Another alternative to reading ufw logs is though grep command:
grep -i ufw /var/log/syslog
grep -i ufw /var/log/messages
grep -i ufw /var/log/kern.logufw logging level
UFW supports the following 5 different logging levels:
- off: disables ufw logging
- low: logs all packets matching logged rules and blocked packets which does not match the defined policies
- medium: In addition to logs supported by low level, medium level logs contain logs for all new connections, invalid packets, allowed packets not matching the defined policy.
- high: logs all medium level logs without rate limiting and all packages with rate limit.
- full: logs all packets without rate limit.
By default, the low level is set as low. We can change the level of log through the command:
sudo ufw logging <LEVEL>Note: Log levels beyond medium tend to generate high volumes of log statements as the output which may result in high disk space utilization on the system.
ufw log rule
UFW supports logging by defined rules. When the parameters of a packet match a defined rule, by default, no logging is performed. UFW allows passing log as parameter to capture all new connections matching the defined rule and log-all parameter to capture all packets matching the rule.
For example, with the above command, we allow ufw to log all new ssh connections.
sudo ufw allow log 22/tcpufw log format
The ufw log statement has the below format:
Jun 17 04:37:25 localhost kernel: [ 765.494242] [UFW BLOCK] IN=wlan0 OUT= MAC=33:33:00:00:00:01:74:83:c2:e4:f8:35:86:dd SRC=fe80:0000:0000:0000:7683:c2ff:fee4:f835 DST=ff02:0000:0000:0000:0000:0000:0000:0001 LEN=200 TC=0 HOPLIMIT=1 FLOWLBL=0 PROTO=UDP SPT=45718 DPT=10002 LEN=160The initial value indicates the date, time, and hostname of the system. Additionally, the subsequent fields represent:
- IN: If contains a value, it indicates that the network interface that the packet arrived on
- OUT: If contains a value, it indicates an outgoing event
- MAC: combination of source and destination mac addresses
- SRC: IP address where the packet came from
- DST: IP address of the packet destination (should be your machine’s IP address)
- LEN: Length of packet
- TOS: Type of service
- TTL: Time to live, represents the number of hops to different routers
- ID: Identification number
- PROTO: packet’s protocol for transmission, eg, TCP/UDP
- SPT: source port of packet
- DPT: destination port of packet
- WINDOW: size of the packet for the protocol
Conclusion
UFW provides a command-line interface for accessing iptables on Linux. It contains tools for administering the network. Logging on ufw allows the user to inspect the incoming and outgoing packets.
In this tutorial, we covered details about different fields captured through the log statements which allows us to inspect the packets in detail. We also explored different levels of logging with ufw and described how levels beyond medium are not the answer available for use.



Comments