Linux treats every object as a file and every file has an owner and a set of file permissions. However, assigning and managing Linux file permissions can be a tricky situation. Setting appropriate permissions is very important to ensure the absolute safety of your critical data. All the users, except for the owner and a user with root privileges, has limited privileges to files and directories. You must have sudo privileges to elevate your privileges. You can also manage permissions using the SUID bit.
In this tutorial, we will learn about the SUID bit and how to set/unset the SUID.
What is SUID Bit?
SUID, also known as Set Owner User ID, is a permission bit that you can set on executable files. SUID enables other users to run executable files with the same permissions as the owner of the file, instead of the permissions of the other user.
SUID is a special permission bit for an executable that let other users to execute a file with appropriate file owner execute permissions. In the permission bit, which is usually represented by an x, SUID is represented by an s.
Examples
The file or directory permissions are generally represented by three-character groups: r (read permission), w (write permission), and x (execute permission). If these letters or character groups are present, then the permissions are granted. Instead of the letter, if there is a hyphen (-) present, then the permissions are not granted.
Apart from the usual rwx file permissions, Linux also supports some special file permission that you can use for certain scenarios, including SUID.
The following example shows you how the SUID permission is displayed:
ls -l /usr/bin/passwd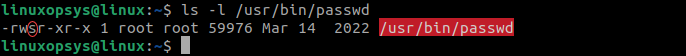
The passwd executable is owned by the root user and the root group. In general, only the root access is enabled or the users with the sudo privileges can run the passwd command. However, the s letter in the user permissions, you do not require the sudo privileges to run the passwd command to change your own password.
Some other examples of the commands that use the SUID are:
ls -l /bin/mount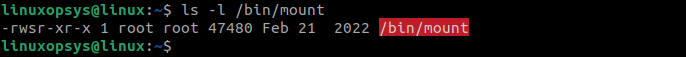
ls-l /bin/su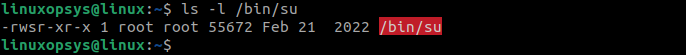
These examples show that the SUID bit is set for the commands/executable files and they will have different permissions than the regular files.
How to Set the SUID bit
When you set the SUID on an executable, the file is run with the same permissions as the file owner. You can set SUID using the chmod command, either using the octal method or symbolic method.
Octal Method
Follow this procedure to set SUID on an executable file:
1. Create a new executable file named script.sh.
vi script.sh2. Set the regular permissions for the executable file:
chmod 0777 script.sh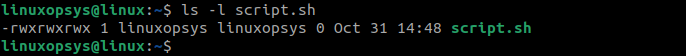
This implies that we have set read permissions, write permissions, and executable permission for the owner, the group, and other users. As you can see, the SUID bit is not set on script.sh.
3. Set the SUID bit by using the chmod command:
chmod 4755 script.sh4. Verify that the SUID is set on the script.sh file:
ls -l script.sh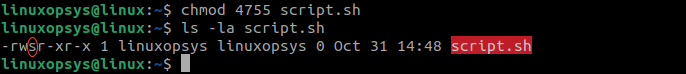
Symbolic Method
If you are not comfortable with using the octal method to set the SUID bit, then you can also use the symbolic method. It is easy and there is no risk of updating the other existing permissions.
1. Create a new Perl script named executable.pl:
vi executable.pl2. Set the SUID bit by using the following command:
chmod u+s executable.pl3. Verify that the SUID is set on the executable.pl file:
ls -l executable.plHow to Remove SUID bit
You can remove the SUID using either the octal method or the symbolic method. To use the octal method to unset SUID, use this command:
chmod 0755 script.sh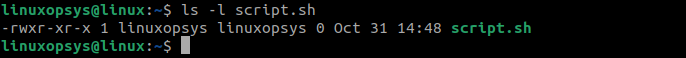
To use the symbolic method to unset SUID, use this command:
chmod u-s executable.pl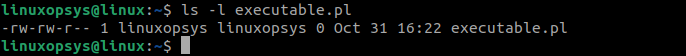
As you can see in these examples, the s bit is removed from the permissions.
Find Files with SUID Bit Set
Use the find command to search for all the files with the SUID. The following command lists all the files with SUID bit set in the current directory:
find . -perm /4000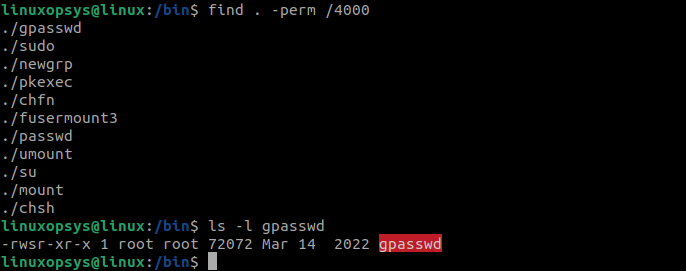
As you can see in the output of the ls -l command, the s bit is set in the permissions.
Conclusion
The SUID, SGID, and sticky bit are special permissions that help you control the security of the files and directories in Linux. Some of the default executable files already have the SGID bit set, for example, passwd, ping, mount, and su. When you manually create an executable file for your programs, then you can set the SGID bit manually by following the examples described here.




Comments