SSH is a network protocol for securely logging into a remote machine and executing commands. It is designed and created to provide the best security when accessing another computer remotely.
The SSH verifies the server's identity, generates a shared session key for data encryption, and authenticates the client using public-key cryptography, ensuring secure and confidential communication between the two parties over a potentially untrusted network.
To use it, the destination machine should have an SSH server application installed, as SSH operates on a client-server model. An SSH server, by default, listens on the standard TCP port 22. SSH client is by default available on all Linux distributions.
In this tutorial, we learn SSH Command in Linux with usage examples.
Prerequisites
- An SSH client.
- An SSH server.
- IP address or name of the remote server.
1. SSH to a Remote Server
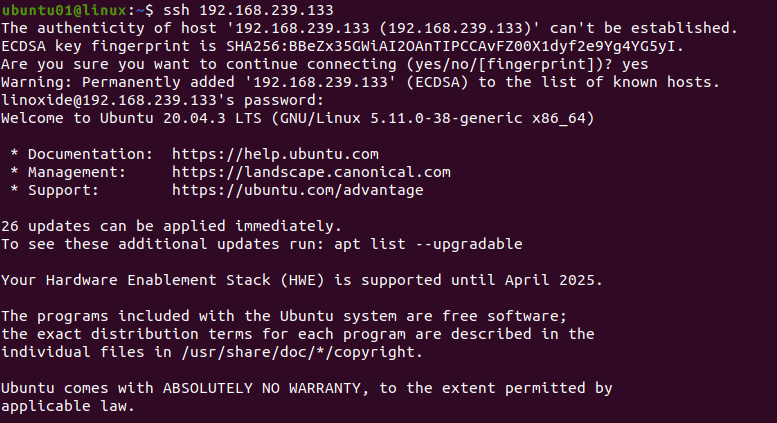
A remote server is connected using an IP address or the name of the host. To connect ssh using an IP address, use the following command:
ssh [IP ADDRESS]To connect to ssh using the name, use the following command:
ssh [HOSTNAME]For example, to connect to a remote host using IP address 192.168.239.133, the command would be following.
ssh 192.168.239.133When you first connect to a host, a message appears asking if you want to continue connecting. Type yes, then enter the password for your remote host.
2. SSH with username
SSH uses the current user of the remote server when trying to connect. To connect to ssh with username, use the following syntax.
ssh [USERNAME]@[HOSTNAME/IP ADDRESS]For example, to connect to the remote host with IP address 192.168.239.134 with a username named kali, use the following command.
ssh [email protected]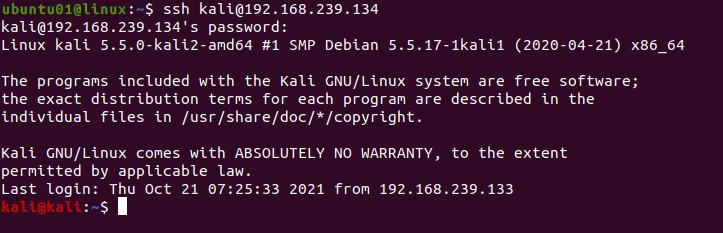
3. SSH with a different Port number
The SSH server listens to TCP port 22 by default but if you wish to change it, you need to specify the port in the command.
To connect to a remote host using a different port number, use the -p flag as shown in the following syntax.
ssh [IP ADDRESS/HOSTNAME] -p [PORT NUMBER]For example, to connect to the remote host with an IP address of 192.168.239.134 using port number 223, use the following command.
ssh 192.168.239.134 -p 223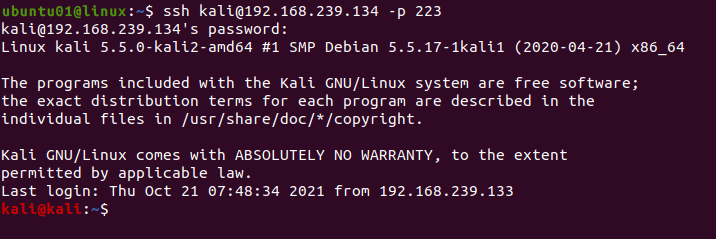
4. SSH without password
In three simple steps, you can connect to your remote host using ssh without a password. The three steps required to log in to a remote server without entering a password are as follows.
Generate SSH key
To generate SSH keys, ssh-keygen is used which creates the public and private keys. These key pairs are used to authenticate between clients and servers.
To create a pair of keys, enter the following command on the client machine.
ssh-keygen -t rsa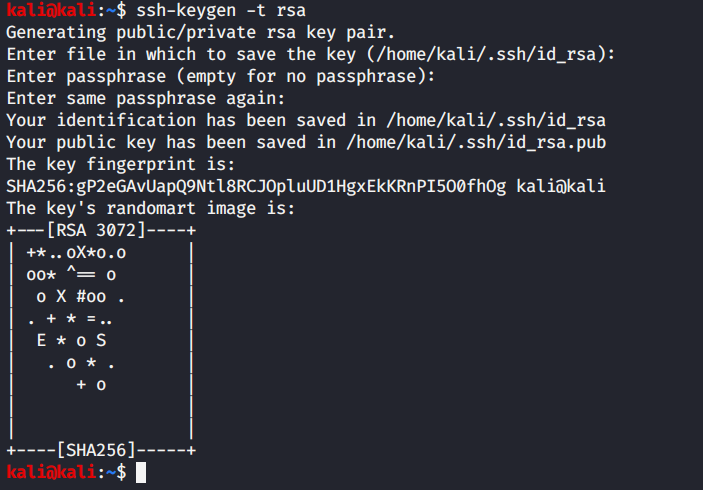
Enter the location and paraphrase, or press enter to use the default settings.
Copy public SSH key
You need to copy the public SSH key to a remote server to use the key pair. To copy the public SSH key to the remote server, use the following syntax on the host machine.
ssh-copy-id [USERNAME]@[HOSTNAME/IP ADDRESS]To copy the SSH key from IP address 192.168.239.134, use the following command.
ssh-copy-id [email protected]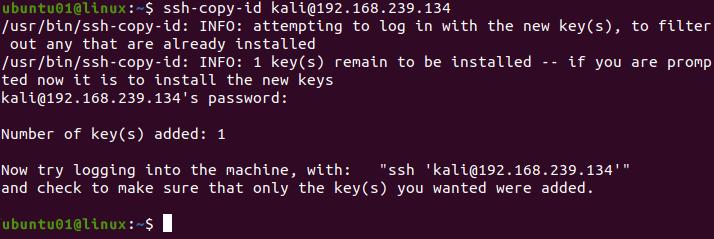
Login remotely without a password
You can now log in to the remote server without a password using the following command.
ssh [USERNAME]@[HOSTNAME/IP ADDRESS]For example, to connect to the remote host with IP address 192.168.239.134 having a kali username, use the following command.
ssh [email protected]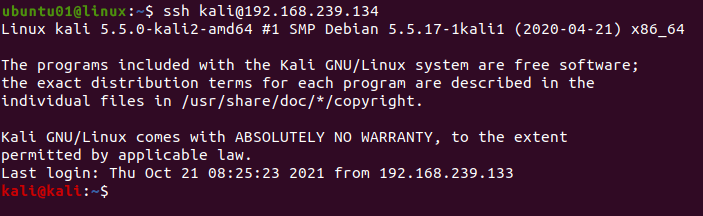
5. Run a Command on Remote Server using SSH
The ssh command can be used to log in to the remote server. It can also be used to execute commands on the remote server.
The basic syntax for executing commands over ssh is as follows.
ssh USER1@SERVER1 COMMAND1ssh USER1@SERVER1 'COMMAND2'ssh USER1@SERVER1 'COMMAND1 | COMMAND2'ssh ADMIN@BOX1 "COMMAND1; COMMAND2; COMMAND3"
To get remote server date and time, use the following syntax:
ssh USER1@SERVER1 dateFor example, to get the date of the kali user from the server of IP address 192.168.239.134, use the following command.
ssh [email protected] date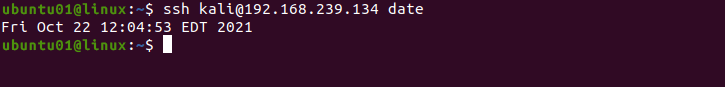
To check the remote server disk space usage, the syntax is as follows.
ssh USER1@SERVER1 'df -H'For example, to get disk space usage of kali user from the server of IP address 192.168.239.134, use the following command.
ssh [email protected] 'df -H'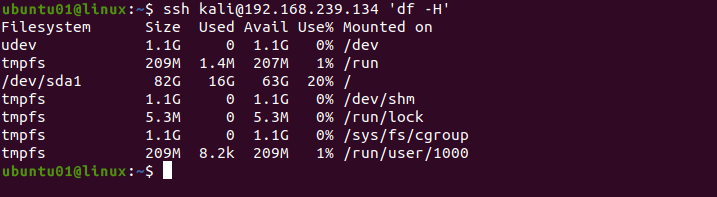
To check the last reboot logs of the remote user, use the following syntax.
ssh USER1@SERVER1 "last reboot"For example, to get the last reboot logs of kali users from the server of IP address 192.168.239.134, use the following command.
ssh [email protected] "last reboot"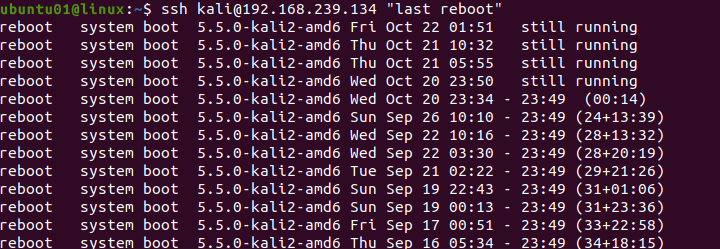
SSH Command line Options
Let us see some of the options available with the ssh command.
ssh -C
Use the -C option with ssh to request compression on all data received or transferred from the remote server, as seen in the following syntax.
ssh -C [USERNAME]@[HOSTNAME/IP ADDRESS]For Example,
ssh -C [email protected]ssh -v
The -v option is used with ssh command to debug the ssh client. The following is the syntax:
ssh -v [USERNAME]@[HOSTNAME/IP ADDRESS]For Example,
ssh -v [email protected]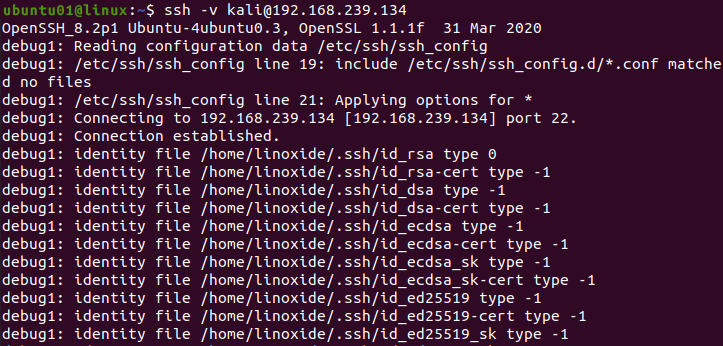
ssh -b
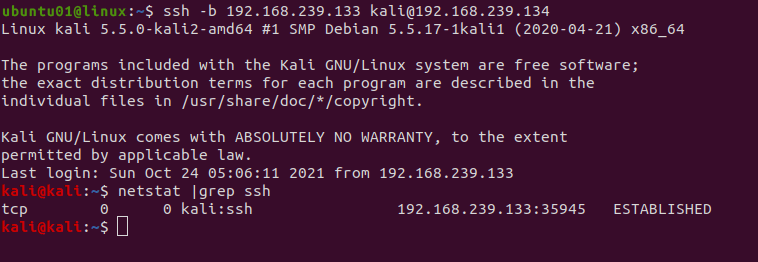
The -b option is used to bind an IP address to an SSH connection. The IP address will be used as the source address of the SSH connection. This is used when a client has more than two IP addresses and you might not know which IP address is used to create a connection to the SSH server.
For example,
ssh -b 192.168.239.133 [email protected]The command will bind the IP address to the remote server. We can check it using the netstat |grep ssh command to check the connection.
ssh -F
The -F option is used along with ssh command to specify a per-user configuration. The default configuration file is ~/.ssh/config.
To use a specific configuration file, use the -F option in the following manner.
ssh -F [File Location] [USERNAME]@[HOSTNAME/IP ADDRESS]For Example,
ssh -F /etc/ssh/ssh_config.d [email protected]ssh -L
The -L option is used for local port forwarding. Local port forwarding allows us to route traffic from our host to a destination port via a proxy.
The basic syntax for local port forwarding is the following.
ssh -L [LOCAL_IP:]LOCAL_PORT:DESTINATION:DESTINATIONPORT [USERNAME]@[HOSTNAME/IP ADDRESS]For example, run the following command to connect to the remote host on port 3306 of kali user with IP 192.168.239.134 from the localhost 192.168.239.133 on port 3336.
ssh -L 3336:192.168.239.133:3306 [email protected]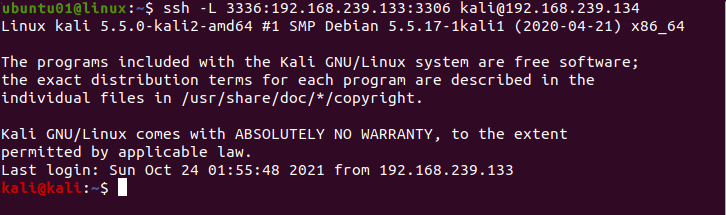
ssh -R
The -R option is used along with the SSH command to enable remote port forwarding. This means you can forward a port on the remote server to a port on your local machine, which is then forwarded to a port on the destination machine.
The basic syntax for remote port forwarding is the following.
ssh -R [REMOTE:]REMOTE_PORT:DESTINATION:DESTINATION_PORT[USERNAME]@[HOSTNAME/IP ADDRESS]
For example,
ssh -R 3336:192.168.239.133:3000 [email protected]The command will make ssh listen to the ssh server in port 3336, and tunnel all traffic to 3000 port.
ssh -C -D
The -D option enables dynamic port forwarding. The usual SOCKS port is 1001, however, any port number can be used; nevertheless, some programs will only work on the 1001 port.
The basic syntax for dynamic forwarding is as follows.
ssh -D [LOCAL_IP:]LOCAL_PORT [USERNAME]@[HOSTNAME/IP ADDRESS]For example,
sudo ssh -C -D 1001 [email protected] The -D specifies dynamic port forwarding in 1001 port and -C enables compression.
ssh -X
The -X option is used along with ssh for X11 forwarding. The following is the syntax for X11 forwarding.
ssh -X [USERNAME]@[HOSTNAME/IP ADDRESS]Use the following command, to enable X11 forwarding on the kali user with IP address 192.168.239.134.
ssh -X 192.168.239.134ssh -Y
The -Y option is used along with ssh for Trusted X11 forwarding. This means that remote X11 will have full access to the original X11 display.
ssh -Y [USERNAME]@[HOSTNAME/IP ADDRESS]Use the following command, to enable Trusted X11 forwarding on the kali user with IP address 192.168.239.134.
$ ssh -Y 192.168.239.134
ssh -o
The -o option can be used with other options.
For example,
ssh -o "batchmode=yes" [email protected]If you use ssh -o "batchmode=yes," the command will run successfully on the remote machine if passwordless connectivity is enabled, otherwise, it will return an error.
Some of the most important command-line options are shown in the following table.
| Options | Description |
|---|---|
| -A | Enables the authentication agent connection to be forwarded. |
| -a | Disables the authentication agent connection to be forwarded. |
| -b | Used to bind source addresses. |
| -C | Enables data compression. |
| -c cipher_spec | Specifies the cipher specification for encrypting the session. |
| -D | Responsible for dynamic application-level port forwarding. |
| -E log_file | Appends debug logs to log_file instead of standard error. |
| -F config file | Specifies a per-user configuration file. |
| -g | Allows remote hosts to connect to local forwarded ports. |
| -i identity_file | Reads the private key for public-key authentication. |
| -j | Specifies a ProxyJump configuration directive. |
| -l login_name | Specifies the user to log in to the remote machine. |
| -p port | Used to specify the port to connect to the remote host. |
| -q | Activates quiet mode. |
| -V | Verbose mode. |
| -X | Enables X11 forwarding |
| -Y | Enables Trusted X11 forwarding. |




Comments