The ss (socket statistics) command in Linux displays network socket information. When a program or process wants to communicate over the network, it creates a socket and specifies the IP address and port it wants to communicate with.
The ss tool is included under iproute2 package and is the default in most Linux Distributions. To have netstat you need to install net-tools, which are already deprecated. Compared to the netstat command, ss is quicker and simpler to use and provides information in a presentable format. ss fetches directly from the kernel. The ss is not a complete replacement of netstat, some of the netstat command is replaced by ip command.
ss Default Output
The ss command without any options list all open non-listening sockets (e.g. TCP/UNIX/UDP) that have established connection.
$ ssNote: Executing the ss command without any options or filters returns an exhaustive list of TCP sockets with established connections.
We will look at all the columns one by one:
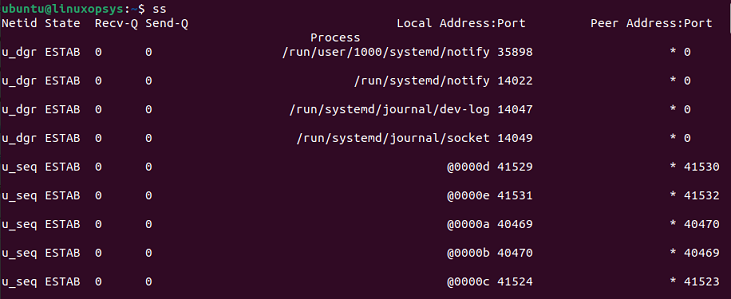
- Netid - It is simply a Socket type. TCP, UDP, SOCK_SEQPACKET, and ICMP are common types of sockets.
- State - The socket's state. Common states of sockets can be SYN-RECV, SYN-SENT, TIME-WAIT, or ESTB (established).
- recv-Q - Tells the number of packets that the queue receives.
- send-Q - Tells the number of packets sent from the queue.
- Local address: port - It shows the address of the local machine and the port.
- Peer address: port - It shows addresses and associated port numbers of the remote machines.
Syntax
ss [Options] [Filters]Using ss Command
1. List network connections
You can list all listening and non-listening network connections using the -a or -all option.
ss -a
2. List listening sockets
To display only listening sockets, which are omitted by default, use -l or --listen option.
ss -l
3. List TCP connections
To display the TCP socket connection, use the -t or --tcp option.
ss -t
To display the list of all the TCP connections, you can use the -a and -t options. This includes all states of the socket.
ss -at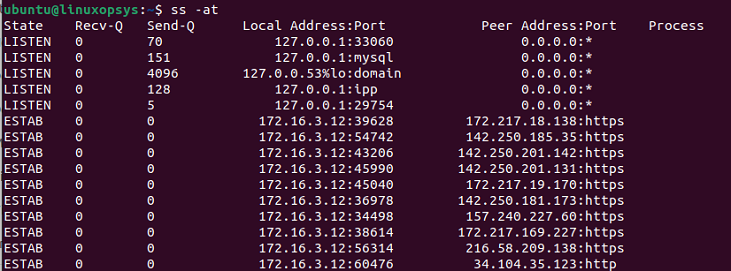
To display the TCP connection for all the listening states, combine -l and -t options.
ss -alt4. List all listening TCP connections
To display the TCP connection for all the listening states, combine -l and -t options.
ss -alt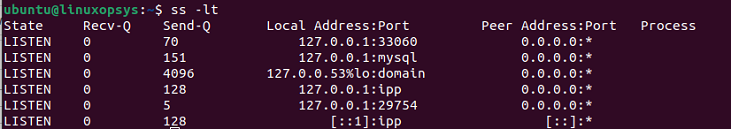
5. List UDP connections
To display the UDP socket connection, use -u or --udp option.
ss -uTo display the list of all the UDP connections, use -a and -u options. This includes all states of the socket.
ss -au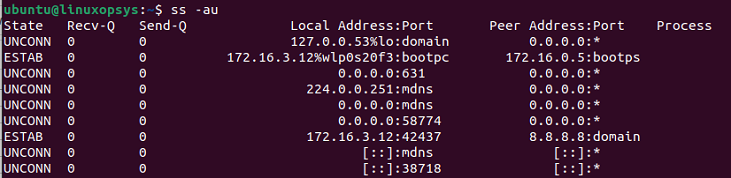
6. List all listening UDP connections
You can combine -l and -u to display the UDP connection for all the listening states.
ss -lu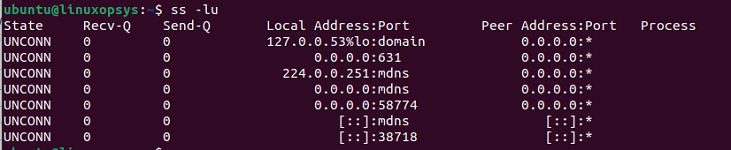
7. List Unix sockets
To display all the Unix sockets, you can use the ss command along with -f unix or -x.
ss -f unix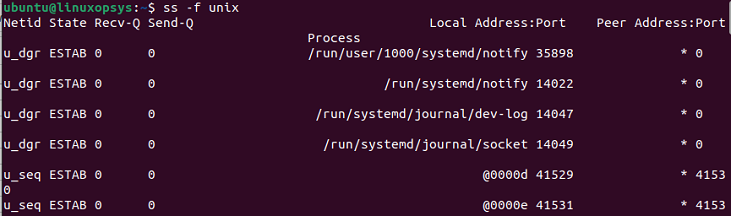
8. List raw sockets
To display all the Raw sockets, you can use -w or --raw option.
ss -w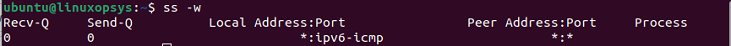
9. List the connection of an IP address
We can use ss command to display the list connection of a specific destination or source IP address.
For example to list connection of destination IP address:
ss dst 157.240.227.60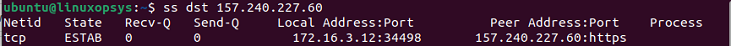
For example to list connection of source IP address:
ss src 192.168.18.15110. List IPv4 and IPv6 socket connections
If you want to display the list of IPv4 socket connections use -4 option and -6 to display the list of IPv6 socket connections.
To display IPv4 socket connection list:
ss -4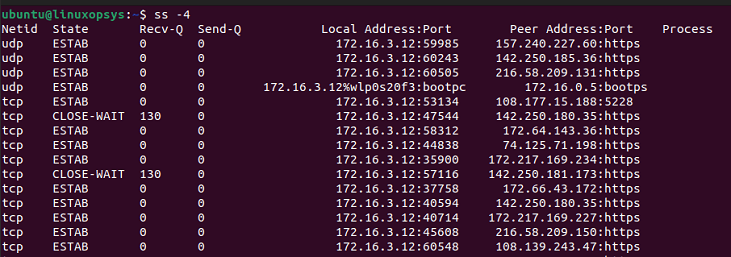
To display the IPv6 socket connection list:
ss -6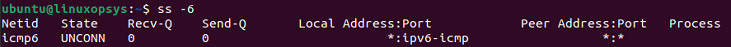
To list all the IPv4 TCP connections, you can use the following example.
ss -at4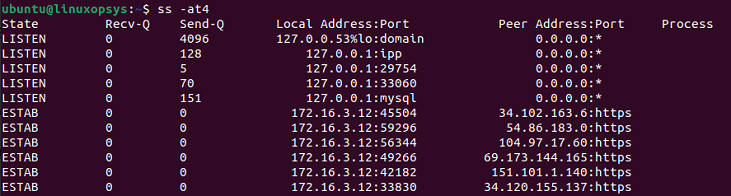
11. Identify processes
You can find the processes of sockets using the -p option along with the ss command. To identify the process, you will need sudo permission.
sudo ss -t -p 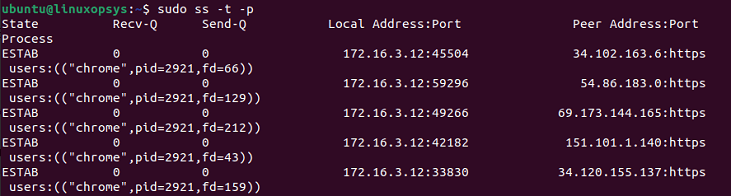
12. List connections with no hostname resolution
To resolve the numeric address/ports use -r (resolve) option. Whereas the -n option does not try to resolve service names.
Here in the example, you can see the difference between the two:
$ ss -tn
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
ESTAB 0 0 74.208.235.196:22 48.192.234.17:60216
$ ss -tr
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
ESTAB 0 64 li82-186.members.linode.com:ssh n47-172-231-17.sun4.vic.optusnet.com.au:60317
$13. Filter by connection
The ss command allows advanced filtering of results and searching for specific ports or TCP states.
Filter using TCP states
To filter TCP connection with state listening, type:
ss -t state listening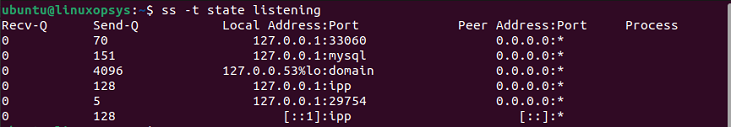
You can also use the grep command to filter conventionally. I'm showing all the TCP connections in the state of listening here:
ss -at | grep LISTEN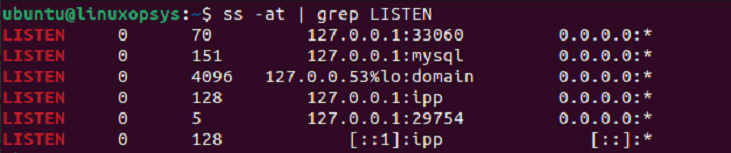
To display established ssh port connections:
ss -tr state established '( dport = :22 or sport = :22 )'Filter by port number
Filter for a specific destination port number or port name:
ss <options> dst :<port number or name>For example, use a port name:
ss dst :https
ss Command Options
-h: Displays a list of all options.-V: Displays the version information.-n: Service names are not resolved (numeric output).-r: Host names are resolved (resolved output).-a: Displays all sockets.-l: Displays all listening sockets.-o: Displays timer information.-e: Show detailed socket information.-m: Show socket memory usage.-p: Show process using the socket.-i: Show internal TCP information.--tipcnfo: Show internal TIPC socket information.-s: Show socket usage summary.-b: Show BPF filter socket information.-E: Continually display sockets as they are destroyed.-Z: Display process SELinux security contexts.-z: Display process and socket SELinux security contexts.-N: Switch to the specified network namespace name.-4: Display only IP version 4 sockets.-6: Display only IP version 6 sockets.-0: Display PACKET sockets.-t: Display only TCP sockets.-M: Display only MPTCP sockets.-S: Display only SCTP sockets.-u: Display only UDP sockets.-d: Display only DCCP sockets.-w: Display only RAW sockets.-x: Display only Unix domain sockets.-f FAMILY: Display sockets of type FAMILY. FAMILY can be {inet|inet6|link|unix|netlink|vsock|tipc|xdp|help}.-K: Forcibly close sockets, display what was closed.-H: Suppress header line.-O: Socket's data printed on a single line.-D FILE: Dump raw information about TCP sockets to FILE.-F FILE: Read filter information from FILE.
State Filters
The state filters of ss command allow users to construct specific sets of matching states.
Examples:
Display all established TCP connections:
ss state establishedDisplay all sockets except for listening and closed:
ss state connectedDisplay all TCP sockets in close-wait state:
ss state close-waitDisplay all listening TCP sockets on port 80:
ss -l -t -p -o state listening '( sport = :80 )'- established: Represents an established TCP connection.
- syn-sent: Indicates that a TCP connection initiation has begun, and the SYN packet has been sent.
- syn-recv: Indicates that a TCP connection initiation has begun, and the system has received a SYN packet.
- fin-wait-1: Indicates that the socket is closed, and the system is actively closing the connection, waiting for the remote end to acknowledge the FIN packet.
- fin-wait-2: Indicates that the connection has been closed locally, and the system is waiting for a connection termination request from the remote end.
- time-wait: Indicates that the socket is closed but is waiting for any remaining packets to arrive before transitioning to the closed state, preventing delayed packets from being misinterpreted.
- closed: Indicates that the socket is closed and not in use.
- close-wait: Indicates that the socket has been closed by the remote end, and the local end has initiated the close sequence.
- last-ack: Indicates that the local end has received a FIN from the remote end and acknowledged it, waiting for the remote end to acknowledge the FIN packet.
- listening: Indicates that the socket is open and listening for incoming connections.
- closing: Indicates that the socket is closed, and the system is waiting for the acknowledgment of the ACK packet sent to the remote end.
Additionally, the following state filters are available:
- all: Matches all states.
- connected: Matches all states except for listening and closed.
- synchronized: Matches all connected states except for syn-sent.
- bucket: Matches states that are maintained as minisockets, such as time-wait and syn-recv.
- big: Matches states opposite to bucket.




Comments