Linux groups are collections of users that you can use to control the permissions. Groups let you define permissions at the group level, so you do not have to set permissions for each user individually. Along with the usual read, write, and execute permissions for a group, use the Set-Group Identification (SGID) special executable permission. SGID bit assigns the groups permissions to the user who is executing the command, file, or application.
In this tutorial, we will learn about the SGID bit in Linux and how to set/unset this special permission bit.
What is the SGID Permission
SGID is a special permission bit that you can set on the groups. When you set SGID on an executable file, it enables the user to execute the file with the same permissions as the group. SGID permission works like SUID permission.
The only difference is that the SGID is set on the group. SGID has different implication on files and directories.
SGID on Files
When you enable SGID on a file, it has the same impact as the SUID permission bit. When a user runs a file with SGID set, the file executes with the same ownership as the group of the file, regardless of who is running the file.
SGID on Directories
When you set SGID on a directory, all the files that you create in that directory will have group ownership of the directory owner. It creates collaborative directories. As you add users to the owner group, these users will have execute permission on the files in these directories and its subdirectories because the group has an SGID permission set.
SGID Examples
SGID is set on an executable file to allow the users to have the same file permissions as the group/file owner. The SGID permission bit is represented by an s, instead of an x in the group permissions of the file or the directory.
The following command example shows SGID set by default on the /var/mail directory:
ls -ld /var/mail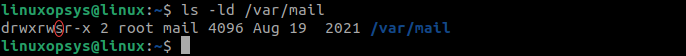
This directory is owned by the root user and the mail group. All members of the mail group can access and execute any of the files in the /var/mail directory, along with the root user.
How to Set SGID
You can enable SGID on a file or a directory either using the octal method or a symbolic method. The result will be the same irrespective of the method you use.
Octal Method
Follow this procedure to enable SGID using the octal method on a directory:
1. Create a new directory named scripts:
mkdir scripts2. Set the regular permissions on the directory:
chmod 0777 scripts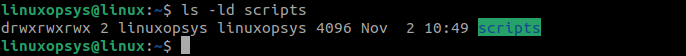
The permissions here show that we have assigned read, write, and execute permissions for the directory owner, all members of the group, and other users.
3. Enable SGID by using the chmod command:
chmod 2755 scripts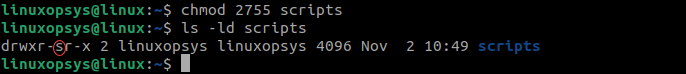
Symbolic Method
Follow this procedure to enable SGID using the symbolic method on a file:
1. Create a new executable file named sort.sh:
vi sort.sh2. Check the current file’s executable permission for sort.sh:
ls -ld sort.sh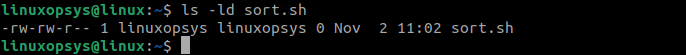
3. Enable SGID by using the chmod command:
chmod g+s sort.sh4. Verify that SGID is set:
ls -ld sort.shHow to Remove SGID
You can remove SGID to revoke special permissions from the files or directories. You can either use the octal method or the symbolic method to unset SGID.
The following command example removes SGID bit using the octal method:
chmod 0745 scripts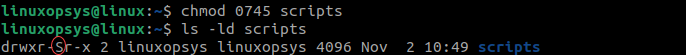
The S (capital S) permission letter in the permissions indicate SGID is not set. The 0 before the permission bit removes special permissions.
The following chmod command removes SGID bit using the symbolic method:
chmod g-s sort.sh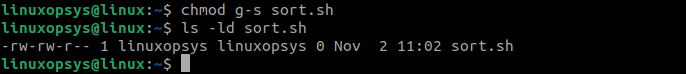
How to Find Files with SGID Permission
Use the find command to list all the files or directories that have the SGID bit set. The following example shows a list of all the files with SGID bit in the current directory:
find . -perm /2000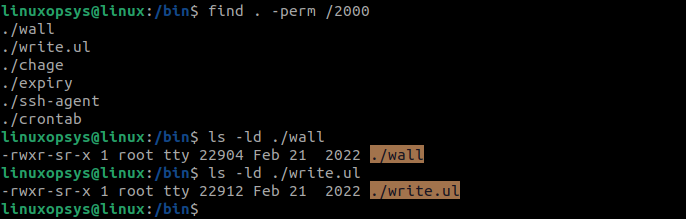
Alternatively, use permission set to 6000 to find files that have both SUID and SGID set.
Conclusion
The special permissions in Linux are very helpful in ensuring the complete safety of your files and directories. The SUID and SGID bit permissions make sure that your executable files have appropriate permissions for the owner, group, and other users. You must be very careful with the regular permissions while setting and removing the SGID.




Comments