Smartcard has been quite common these days. You are using them in your office for access and logins, you’re using them as your Debit/Credit Cards, you are using them to access your satellite tv / set-top boxes, you’re using them as your Government ID cards etc.
In this guide, we'll learn how to set up smartcard authentication in Linux.
Smart card
A smart card is a type of secure hardware device that is used to store and process information. It has a built-in microprocessor chip.
Smart card provides tamper-resistant storage for protecting private keys, it is considered a secure and better alternative to password-based logins.
One common use of smart cards is for authentication, where the card is used to verify the identity of the user. To enable smartcard authentication on your domain, please follow vendor instructions.
The card will authenticate users, the certificate will carry a Key Exchange private key type. Install the vendor’s drivers and software and you will be able to store keys to the smartcard.
How smartcard works
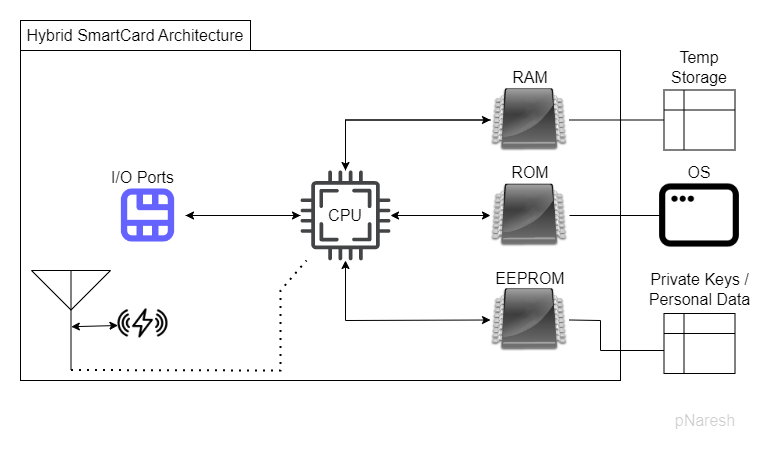
A hybrid smartcard can be used by inserting it into a card reader or via RFID mechanism. Card reader or IFD (Interface device) provides power and clock signals to the card and is responsible for opening a half-duplex communication channel between Computer and OS on the card. Smartcard OS is a set of few commands and the communication is buffered into the RAM.
Below is a sample diagram to illustrate a hybrid smartcard architecture.
Set up Smart Card Authentication on Linux
Here we will use SSSD. It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use SSSD for smart card authentication.
01. Configure SSSD authentication with your AD, and ensure you have added your 3rd party CA certificate to the node (/etc/ssl/certs/xxx.pem).
02. On the node, install the following packages.
pcscd, opensc, opensd-pkcs11 and p11-kit-modules
03. Remove /etc/pki/nssdb, touch it, and chmod to 0644
Now we’ll use certutil and modutil to create and modify our NSS db. These packages are part of libnss3-tools package.
Certutil - is a command line utility that you can use to manage NSS keys and NSS tokens.
Modutil – is a command line utility that allows you to manage PKCS#11 module information within the security module databases.
The new version of SSSD is based on SQL but Gnome uses old ones
04. The following command creates an empty NSS db at the given path.
certutil -d sql:/etc/pki/nssdb -N –empty-password05. With modutil we'll add ‘opensc pkcs11 module’ to our NSS db we just created
modutil -add ‘opensc pkcs11 module’ -libfile opensc-pkcs11.so -dbdir sql:/etc/pki/nssdb06. Add Certificate to database
Now let’s assume you’re following best practices and you have different CAs for user authentication, signature, and root CA. Let’s add these to our NSS database. If you’re just testing, add your root CA and it’ll do.
Certutil -d sql:/etc/pki/nssdb -A -n <your third party user auth CA> -t CT,CT,CT -a -I /etc/ssl/certs/<your user authentication CA.pem>Certutil -d sql:/etc/pki/nssdb -A -n <your third party root CA> -t CT,CT,CT -a -I /etc/ssl/certs/<your root CA.pem>Certutil -d sql:/etc/pki/nssdb -A -n <your third party user signature CA> -t CT,CT,CT -a -I /etc/ssl/certs/<your user signature CA.pem>09. Touch an empty file pam_preauth_available in /var/lib/sss/pubconf/
Why?. SSSD which you’ve already configured with your AD will try to use the suitable prompting depending on your configuration. Preauth and Step #10 will allow it to use smartcard authentication. SSSD with these configuration figures out that smartcard with a certificate is suitable to authenticate a user and then it will prompt for smartcard PIN.
10. Ensure your sssd.conf have the following lines:
[pam]
Pam_cert_auth = true
Pam_cert_auth_db_suffix = sql:/etc/pki/nssdb
Create a new sections in sssd.conf –
[certmap/<your domain>/smartcard]
Matchrule = <SAN:ntPrincipalName>@yourdomain
Maprule = (sAMAccountName={subject_nt_principal.short_name}
Priority = <choose a priority here e.g. 5>11. Ensure your common-auth in pam.d is carrying
For auth – pam_sss.so allow_missing_name forward_pass along with other requisite/required/optional config.
As you are already aware of that pam_sss.so is PAM interface to the SSSD. Here we are configuring it so that it allow other PAM modules to use the entered credentials.
12. Assuming you’re using gnome, so add an dconf entry to ensure removal of smartcard locks the system
[org/gnome/settings-daemon/peripherals/smartcard]
Removal-action=’lock-screen’13. Pam-auth-update, reboot, and test it.
Conclusion
Here we learned how to set up smart card authentication in Linux. It involves an AD eco-system, a physical smart card to store your keys and certificate, card reader (and drivers if applicable).
On a usual Linux node, the OS will communicate with card via PC/SC protocol and low-level CCID driver. That's where we'll need the opensc tools - to communicate with the card and to manage data structures/data objects of your PIN, Keys, and certificates. The system will use the PKCS#11 cryptographic token interface with PAM and SSSD to authenticate a user.




Comments