SELinux adds additional security enhancement through a set of kernel modifications and user-space tools. This is often useful for web servers and systems that are more exposed.
How do you modify and alter SELinux settings on your system? In this tutorial, we learn about semanage command in Linux with useful examples.
semanage Command
Semanage is a tool used to configure certain elements of SELinux policy without modifying or recompiling policy sources. It can help to adjust port contexts, booleans, and file contexts, etc.
Commonly used configurations include mapping Linux users to SELinux user identities and security context mappings for network ports, interfaces, hosts and file context mapping.
Syntax
semanage {user|port|fcontext|boolean|permissive...} -l [-n]Where,
port - Manage network interface type definitions.
fcontext - Manage file context mapping definitions.
boolean - Manage booleans to selectively enable functionality.
permissive - For process type enforcement mode
User - Manage roles and levels for users.
Install semanage
Semanage is not preinstalled on most Linux distributions and you must install this tool manually. It is part of the policycoreutils-python (in older Linux distributions) and policycoreutils-python-utils (later distributions). These packages contain SELinux core policy utilities.
If the semanage is not already installed on your Linux computer, then you may get the following error semanage: command not found.
RHEL 7 and older versions, type:
yum install policycoreutils-pythonRHEL 8 and later versions, type:
yum install policycoreutils-python-utilsFedora
dnf install policycoreutils-python-utilsUbuntu / Debian
sudo apt install policycoreutils-python-utilsTo confirm if semanage is installed, type:
semanage -h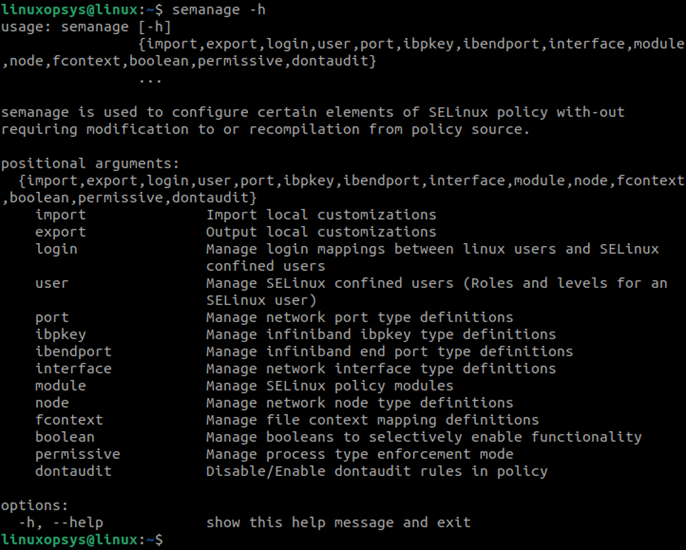
semanage Port
By default, SELinux only allows known services to bind to known ports. If we want to modify a service to use a non-default port we will need to modify the port type with the semanage port command.
You can use these commands to list existing ports, add a new port, range of ports, and delete existing ports.
Listing ports
To list all ports on your Linux computer, type:
sudo semanage port -l
SELinux Port Type Proto Port Number
afs3_callback_port_t tcp 7001
afs3_callback_port_t udp 7001
afs_bos_port_t udp 7007
afs_fs_port_t tcp 2040
afs_fs_port_t udp 7000, 7005
afs_ka_port_t udp 7004
…Creating / Adding port
To create a new port, specify the protocol and the port number:
sudo semanage port -a -t http_port_t -p udp 7956To assign a range of ports to a specific network port, type:
sudo semanage port -a -t http_port_t -p tcp 7957-7959Output
sudo semanage port -lC
SELinux Port Type Proto Port Number
http_port_t tcp 7956, 7957-7959
Listing Customization
Use the -lC option to list only the customizations and to verify that the port is created successfully:
sudo semanage port -lCSELinux Port Type Proto Port Number
http_port_t udp 7956Override Port
Use the -m option to override an existing port, otherwise it is not possible to use the same port number:
sudo semanage port -m -t unreserved_port_t -p tcp 7956Delete Port
Use the -d option to delete a port record:
sudo semanage port -d -t unreserved_port_t -p tcp 7956You can also use the same command to delete a range of the ports:
sudo semanage port -d -t unreserved_port_t -p tcp 7957-7959semanage Fcontext
semanage Fcontext command is used to adjust the SELinux context of files. Changes are written to files located under /etc/selinux/targeted/contexts/files/ directory. Commonly used to update and delete file context. SELinux content (SELinux label) fields are user, role, type, and security level.
You need to run restorecon -v file-name|directory-name to enable the changes.
Examples:
1. To list all the sshd file context mapping definitions, type:
sudo semanage fcontext -l | grep sshd/etc/ssh/primes regular file system_u:object_r:sshd_key_t:s0
/etc/ssh/ssh_host.*_key regular file system_u:object_r:sshd_key_t:s0
/run/sshd(/.*)? all files system_u:object_r:sshd_runtime_t:s0
/run/sshd\.init\.pid regular file system_u:object_r:sshd_runtime_t:s02. Add a new file context mapping definitions for an existing file, type:
sudo semanage fcontext -a -t samba_share_t /tmp/docs.txtWhere the -a option adds a new record and -t option defines the type.
This adds a new entry in /etc/selinux/targeted/contexts/files/file_contexts.local file.
To get the type changed, type
restorecon -v /tmp/docs.txtTo list the information, run:
ls -Z /tmp/docs.txt3. To change the directory and its files context type:
sudo semanage fcontext -a -t httpd_sys_content_t "/site(/.*)?"Here we change the directory /site and files to httpd_sys_content_t.
4. To delete the context use -d option.
Example
semanage fcontext -d "/site(/.*)?"To restore to default SELinux run restorecon command as root Linux user.
semanage Permissive
Semanage permissive command is used to place a single domain into permissive mode. It enables you to add or delete SELinux policy permissive modules.
Examples
1. Use the -l option to list all existing permissive modules:
sudo semanage permissive -lBuiltin Permissive Types
Customized Permissive Types
httpd_t
sshd_t2. Use the -a option to move a specific domain to permissive mode:
sudo semanage permissive -a sshd_t3. Use the -d option to delete the permissive mode we just created:
sudo semanage permissive -d sshd_tlibsemanage.semanage_direct_remove_key: Removing last permissive_sshd_t module (no other permissive_sshd_t module exists at another priority).semanage Boolean
Semanage boolean command is used to adjust specific elements of SELinux policies. Commonly used to change parts of SELinux policy at run time.
Examples
1. Use the -l option to list all the Booleans in the current SELinux policy:
sudo semanage boolean -l | grep httpdallow_httpd_anon_write (off , off) Determine whether httpd can
modify public files used for public file transfer services. Directories/Files must be labeled public_content_rw_t.
allow_httpd_apcupsd_cgi_script_anon_write (off , off) Determine whether the script domain can modify public files used for public file transfer services. Directories/Files must be labeled public_content_rw_t.
allow_httpd_awstats_script_anon_write (off , off) Determine whether the script domain can modify public files used for public file transfer services. Directories/Files must be labeled public_content_rw_t.2. Use the -m option to change the Boolean:
sudo semanage boolean -m --off sshd3. Use the -lC option to list all the Booleans that are customized locally:
sudo semanage boolean -lC



Nice blog.
Thanks