Are you preparing for a Linux interview? We have prepared some of the commonly asked Linux interview questions and their answers.
1. What is Linux and used for?
Linux is a free and open-source operating system that is based on the Linux kernel. It is a piece of code that sits between applications and hardware. It can manage hardware such as CPU, memory, and storage.
Linux is commonly used as web servers, database servers, file servers, and email servers.
2. What are the main components of Linux operating system?
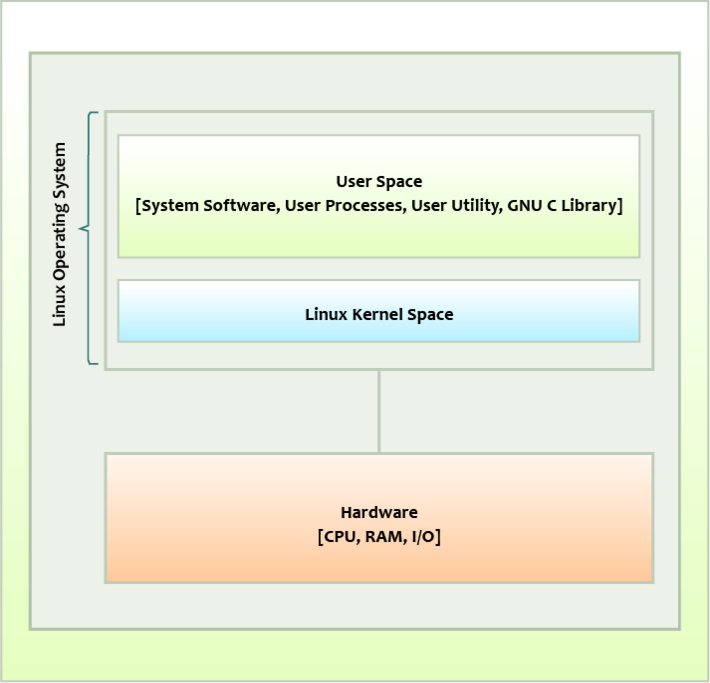
Linux constitutes of 2 main components:
Kernel: This is the core of the Linux system. It's responsible for interacting with the hardware components and ensuring the operating system communicates with hardware devices.
User Space: Consists of system components and libraries that the operating system uses to interact with the kernel. System components consist of init daemon, system daemons, window manager, and graphics. The C standard library includes fopen, malloc, execv, and more.
3. What is the Linux Kernel?
A Linux kernel is the core of the Linux system. It interfaces the underlying hardware with the operating system.
The types of kernel available are the monolithic kernel, microkernel, hybrid kernel, nano kernel, and exo kernel.
4. What is the difference between Linux and Unix?
Linux is a clone of the UNIX system from which Linux is derived. While Linux is open source and free to use, UNIX is a proprietary operating system.
Some more important differences:
| Linux | Unix |
|---|---|
| Linux means the kernel of GNU/Linux. | Unix refers to the original operating system developed by AT&T. |
| Written in C and other programming languages. | Written in C and assembly language. |
| The source is code open source | Mixed |
| Kernel type is monolithic | Could be monolithic, microkernel or hybrid. |
| Cost is free. There are some priced versions available. The corporate charge for support service. | Different costs based on vendor. |
| Linux trademark is owned by Linux Torvalds. | The UNIX trademark is certified by the Open Group. |
| Linux is generally secure. Frequent updates, user permissions, and low market share. | Even more secure due to the fact the source code is not available. |
5. What is inode in Linux?
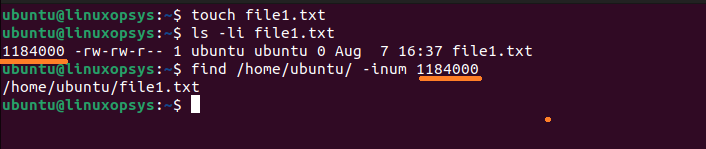
When a file or directory is created in the filesystem, it is assigned with a name and an inode number. The inode is an integer that is unique within the filesystem.
The inode (index node) is a data structure in a Unix-style file system that describes a file-system object such as a file or a directory. That means it doesn't store any data but instead stores its metadata.
To get a listing of an inode number, use ls -i command.
6. What is Linux shell?
A Linux shell is a command interpreter or a program that accepts commands and passes them to the operating system for execution.
To check the shell that you are using, type echo $0 from your terminal.
Bash is not the only shell in Linux. Here is some more Linux shell:
→ Z Shell (zsh)
→ Tcsh/Csh Shell (csh)
→ Korn Shell (ksh)
→ Fish Shell (fish)7. What command to check memory usage in Linux
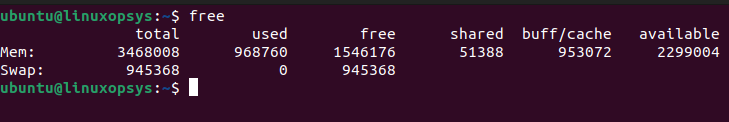
Use Linux free command. It displays a summary of RAM usage such as total, used, free, shared, and swap space.
Alternative commands to check memory usage are vmstat and top.
8. Differences between Softlink and Hardlink?
Some of the differences you can tell to the interviewer are:
- Hardlink cannot be created for directories. A hard link can only be created for a file.
- Symbolic links or symlinks can link to a directory.
- Removing the original file that your hard link points to does not remove the hardlink itself; the hardlink still provides the content of the underlying file.
- If you remove the hard link or the symlink itself, the original file will stay intact.
- Removing the original file does not remove the attached symbolic link or symlink, but without the original file, the symlink is useless
9. Explain 3 file access permission in Linux?
In Linux, there are 3 main types of file permissions: read, write and execute. These permissions can be assigned to either a file or a directory recursively. Being a multi-user system, you can assign these permissions to the root user, groups or even to other users using the system.
Read: The read permission grants users the ability to open and read a file.
Write: Write permission allows a user to open and modify or edit the file's contents and save the changes.
Execute: This allows a user to execute or run the file or a program or shell script which is executable.
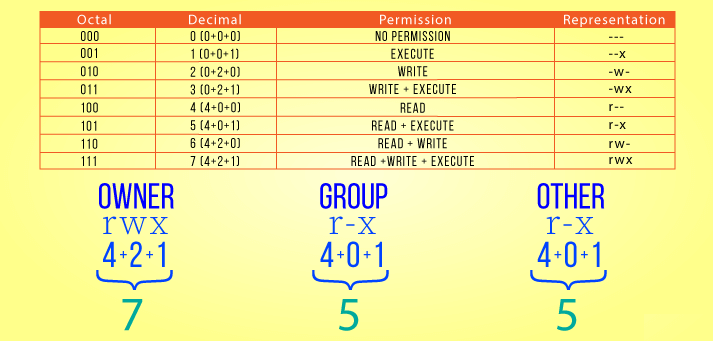
Setting 755 permission means:
owner - Read, Write, and Execute
group owner - Read and Execute
others - Read and Execute
To set file permissions in Linux use chmod command. For example:
chmod 755 filename10. How to create a new directory in Linux?
To create a directory a new directory in Linux use mkdir command.
Syntax:
mkdir directory_nameFor example to create a directory called 'data' run the command:
mkdir data11. How to delete a directory in Linux?
To delete a directory in Linux, use either the rm or rmdir command.
The rmdir command is used to remove empty directories.
To remove a directory and its subdirectories use the recursive option. For example rm -r directory-name
12. How to create a new file in Linux?
There are various ways to create a new file in Linux.
1. Using touch command
To create an empty text file named file1.txt, type:
touch file1.txt2. Using cat command
You can also use cat command followed by the redirection operator >
followed by the name of the file.
cat > file2.txtNext, type the content of the file, and then press CTRL + D to exit the file.
3. Using a text editor such as vi or nano.
13. How to rename a file from Linux Terminal?
To rename files, use the mv command. Basically used to move files. For this to work, the path of the file to be renamed needs to be the same.
mv /data/files/file1.txt /data/files/file2.txt14. How to copy files in Linux?
To copy files in Linux, use the cp command. Use cp command followed by the source file and then place the location where to file to be copied.
In the following example, the contents of file in /source/of/the/file.txt is copied to /destination/of/the/file2.txt.
cp /source/of/the/file.txt /destination/of/the/file2.txtTo copy multiple files in the source directory to another directory:
cp /home/documents/*.txt /backup15. How to list mount devices in Linux?
There are a few ways to list mounted devices in Linux. From the terminal type:
cat /proc/mounts
mount
df -aTh
findmnt16. Which program is used to schedule task in Linux
The cron is a deamon that executes commands at specific dates and times in Linux. You can use this to schedule activities, either as one-time events or as recurring tasks. Crontab is the program used to install, deinstall or list the tables used to drive the cron daemon in a server. Each user can have their own crontab, and though these are files in /var/spool/cron/crontabs, they are not intended to be edited directly.
Here are few of the command line options for crontab.
Edit your crontab file - crontab -eShow your crontab file - crontab -l
Crontab file format consists of six fields separated by white spaces:
<Minute> <Hour> <Day_of_the_Month> <Month_of_the_Year> <Day_of_the_Week> <command/program to execute>The format is explained as follows:
* * * * * *
| | | | | |
| | | | | +-- Year (range: 1900-3000)
| | | | +---- Day of the Week (range: 1-7, 1 standing for Monday)
| | | +------ Month of the Year (range: 1-12)
| | +-------- Day of the Month (range: 1-31)
| +---------- Hour (range: 0-23)
+------------ Minute (range: 0-59)17. What are the basic Vim commands you know?
Basic vim commands are:
| Command | Description |
|---|---|
| i | Enter insert mode to enable editing or adding contents. |
| Esc | Enter command mode to use any commands. |
| Esc + :w | Save the file without exiting. |
| Esc + :q! | Exit Vim without saving the change you made. |
| Esc + :wq | Save the changes and exit Vim. |
| Esc + dd | Delete the current line. |
18. How to add a directory to $PATH variable?
Use the export command to add a directory to $PATH variable. For example, to add bin directory in your Home directory, which needs to add to the PATH variable.
export PATH="$HOME/bin:$PATH"19. What is Grep command
Grep command is used to search text or string of characters in a file. Commonly used with other commands output with piped to be the input.
For example to search any line that contains the bob in the filename
grep 'bob' filename
Using grep with other commands
lsusb | grep Device20. Do Linux Support Regular Expressions
Yes, Linux supports regular expression. Its also called as 'regexp' or 'regex'. Regex are special characters are used with commands to search and match complex patterns.
You can use regular expressions with commands such as grep, awk, sed, rename, tr, etc.
Let me show you a regular expression ^ to match the start of a string. The following examples search for all lines in the file that start with letter l:
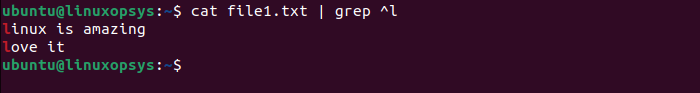
21. What is umask in Linux?
Umask stands for ‘User file creation mask’, which determines the settings of a mask that controls which file default permissions are set for files and directories when they are created.
To display the current mask value, type
umask
To change umask , type umask followed by the required umask numeric value:
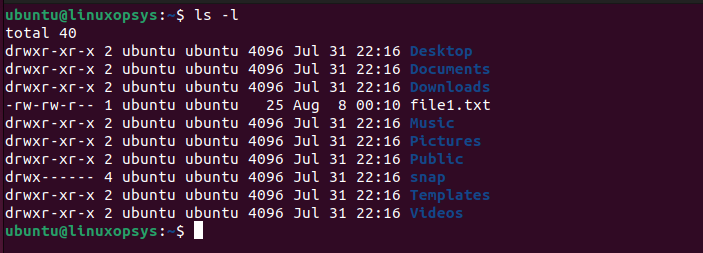
umask <numeric-mask-value>22. What is the output of ls command in Linux?
ls command lists the contents of a directory in Linux. It displays the files and sub-directories inside the directory. When used with other arguments for example ls -l, it can list file type, link count, permissions, owner, group, file size, last modified date, and filename.
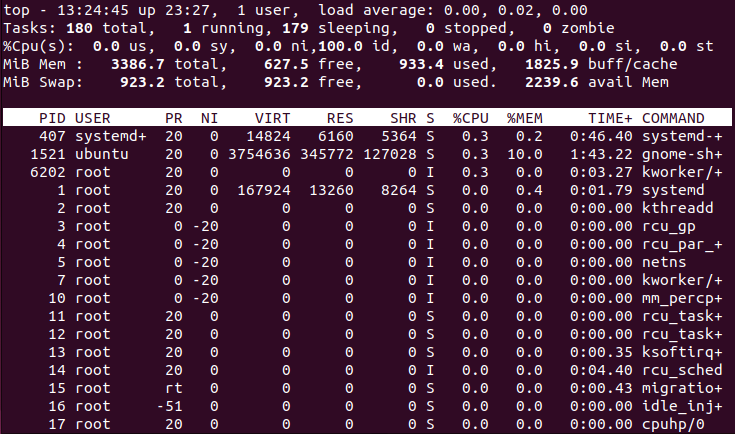
23. What top command output show?
Top commands show the first 4 lines with average system load, tasks, percentage of CPU, memory & swap usage, then followed by a list of all processes.
24. What are the process states in Linux?
Process States as the name suggests the current state that a Linux process is in. There are 4 process states namely Running, waiting, stopped, and Zombie.
25. Command to backup data in Linux (tar command)?
The commonly used commands to back up files are tar and rsync.
Tar creates an archive file and this file can be scheduled to move to a backup storage device.
Rsync can synchronize files and directories to and from the host over a secure shell.
26. How to stop a running process from Linux Terminal?
First, determine the process id using the ps command, then use the kill command.
For example, to stop a process with PID 3836, run the command
kill 383627. What command is used to search files in Linux?
To search files in Linux, type find command with -name option followed by filename you want to search.
Example:
find -name file1.txt28. Command to check service status in Linux?
To check service status in modern Linux distros, use systemctl status service-name command.
For example to check the status of postfix, type:
systemctl status postfix29. How to start a service at startup of Linux?
To start a service on reboot run use systemctl enable service-name command.
For example, to enable apache2 service to start up on system startup, type:
systemctl enable apache230. How to start a service in Linux?
In systemd, to start a service use systemctl start service_name.
For example, to start the Nginx service, run the following command:
systemctl start nginxTo stop the service, type:
systemctl stop nginxTo restart the service, type:
systemctl restart nginx31. How to remote login from Linux client to Linux Server?
ssh username@remote-server-ip-or-hostnameThe client machine from where the connection is made should have the ssh client installed. By default, the client is installed in most Linux distributions. The remote host should have sshd daemon installed (openssh-server) and enabled. Also, make sure the ssh port is enabled in the firewall.
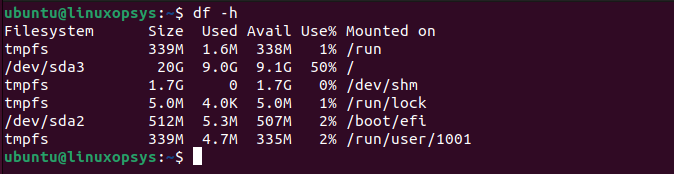
32. How to check disk usage in GB in Linux?
Use df -h command to display disk usage in a human-readable format. This shows disk usage in bytes, MB, GB, and TB.
33. Write a bash script to get Linux version from multiple Linux servers
#!/bin/bash
#we user variable serverlist to keep there path to file with server names
serverlist='server_list.txt'
#we write in variable all server list
servers=`cat $serverlist`
#we use variable result to keep there path to file with result
result='result.txt'
#this print header to file with resilt using \t\t to add 2 tab symbols
echo -e "Servername \t\t kernel version"> $result
#this get each line of serverlist one by one and write to server variable
for server in $servers
do
#this login to server by ssh and get uname -r
kernel=`ssh root@${server} "uname -r"`
#this write server name and kernel version separated by 2 tab to result file
echo -e "$server \t\t $kernel" >> $result
#end of for loop.
done34. What is required for Linux installation?
| Resources | Description |
|---|---|
| Processor | 64bit |
| RAM | 1GB |
| Disk Space | 25GB |
| CD/DVD, USB | For installer media |
| Internet Access | To download packages and updates |
35. How change the owner of a file in Linux?
You need sudo or root access to change ownership of a file. For changing the owner of a file use chown new-owner filename command.
For example to change the owner of the file to a user named www-data, type
chown www-data filenameFor a directory use the -R option to assign permissions recursively. For example
chown -R www-data directory_name36. How to find the current kernel version?
Use -r option with uname command to find the Linux kernel version.

37. How to find the OS version on Linux?
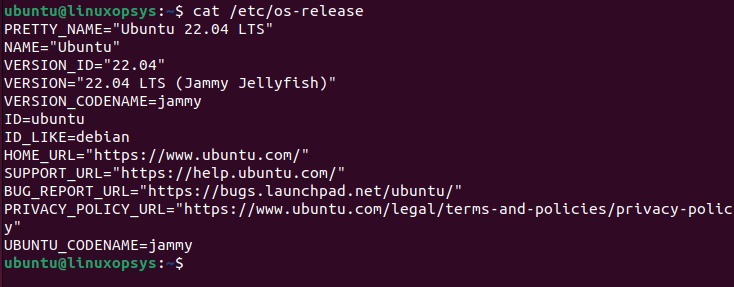
Open the file /etc/os-release using cat or grep to display OS version of Linux.
38. How to show IP address Linux terminal?
The easiest way to find IP address in Linux is to type ip a command from the terminal.
39. What is initrd image?
The initial RAM disk (initrd) is an initial root file system that is mounted prior to when the real root file system is available. The initrd is bound to the kernel and loaded as part of the kernel boot procedure. The kernel then mounts this initrd as part of the two-stage boot process to load the modules to make the real file systems available and get at the real root file system. Thus initrd image plays a vital role in linux booting process.
40. Explain the terms suid, sgid and sticky bit?
In addition to the basic file permissions in Linux, there are few special permissions that are available for executable files and directories.
SUID: If setuid bit is set, when the file is executed by a user, the process will have the same rights as the owner of the file being executed.
SGID: Same as above, but inherits group privileges of the file on execution, not user privileges. Similar way when you create a file within the directory, it will inherit the group ownership of the directories.
Sticky bit: Sticky bit was used on executables in linux so that they would remain in the memory more time after the initial execution, hoping they would be needed in the near future. But mainly it is on folders, to imply that a file or folder created inside a stickybit enabled folder could only be deleted by the owner. A very good implementation of sticky bit is /tmp , where every user has write permission but only users who own a file can delete them.
41. What is systemd in Linux?
systemd is a replaced system for SysV init scripts. It initializes the Linux system and acts as a service manager. Systemd contains programs, services, and libraries such as systemctl, journalctl, Init, Process management, networkd, journald and more.
42. What is SeLinux?
SELinux is an acronym for Security-enhanced Linux. It is an access control implementation and security feature for the Linux kernel. It is designed to protect the server against misconfigurations and/or compromised daemons. It put limits and instructs server daemons or programs what files they can access and what actions they can take by defining a security policy.
43. How to find open files in Linux?
To find open files in Linux use lsof command. It lists information about the files that are opened by various processes. In Unix, everything is a file: pipes, sockets, directories, devices, etc.
By using lsof, you can get the information about any opened files.
List processes that opened a specific file
lsof /var/log/syslogList all open files belonging to processes owned by the user
lsof -u usernameList processes that are listening on a particular port
lsof -i :2544. What is name-based and IP-based virtual hosting?
In name-based virtual hosting, you can host multiple websites on the same IP address. For this to succeed, you have to put more than one DNS record for your IP address in the DNS. On IP-based virtual hosting, we can run more than one website on the same server. Each website has its own IP address.
45. What is the advantage of Network Bonding?
Network Bonding is a Linux kernel feature that allows to aggregate multiple network interfaces into a single virtual link. This is a great way to achieve redundant links, fault tolerance or load balancing networks in the production system. If one of the physical NIC is down or unplugged, it will automatically move traffic to the other NIC card. Similar way the bonding will increase the interface throughput to handle the traffic it is configured in active-active mode.
46. What is /etc/shadow file?
The /etc/shadow file stores the actual password in an encrypted format with some additional properties related to user password. It mainly holds the account aging parameters. All fields are separated by a colon (:) symbol. It contains one entry per line for each user listed in /etc/passwd file.
47. What is passwordless SSH?
Passwordless SSH is an authentication mechanism to interact with remote hosts using a key pair. Instead of prompting for a password, this method allows to authenticate using the public and private key. Using ssh keys to authenticate user identity gives better security than using user/password method.
The private key is placed securely on the system and the public key gets propagated to remote host(s).
48. What is swappiness in Linux?
The swappiness parameter controls the tendency of the kernel to move processes out of physical memory and onto the swap disk. Because disks are much slower than RAM, this can lead to slower response times for system and applications if processes are too aggressively moved out of memory.
swappiness can have a value of between 0 and 100
swappiness=0 tells the kernel to avoid swapping processes out of physical memory for as long as possible
swappiness=100 tells the kernel to aggressively swap processes out of physical memory and move them to swap cache
I hope the Linux interview questions help you with the job interview. Wish you all good luck !!!




Comments