Remote ssh login using the root account is not a good Linux security practice. It poses a security challenge that can render your system vulnerable to attacks.
In this guide, we learn how to disable root login for SSH on Linux.
Why we should disable SSH root login?
A Linux system with remote root access can easily fall victim to brute force attacks. This is where an attacker uses automated scripts to guess the root login password.
Good practice recommends that you disable remote root login to your Linux machine. This prevents an attacker from remotely accessing your Linux server using the root password and, thus, having unlimited control over your system.
The alternative is creating a normal user account with almost all administrative privileges for remote logins. The user needs to be added to the sudo group to have some administrative privileges. This means that an attacker would need to first log in as a regular user and then use the "su" or "sudo" command to gain root access.
Additionally disabling ssh root login helps system admins to track and audit user activities as they act as root.
Prerequisites
Require access to a Linux system via console or ssh. Here for example we are using a Ubuntu system.
Step 1. Terminal Access to SSH Server
The SSH server accepts ssh connections from ssh clients. Once the SSH server is installed with SSH server software (openssh-server package), by default it accepts ssh remote connection for root and for all other users.
Access the terminal of your SSH server:
ssh root@server-ipIf you are logging in using the SSH key authentication method, type:
ssh -i your_private_key root@your_server_ipThe -i option specifies the SSH private key which will be used for authentication with the public key saved on the SSH server.
Step 2. Check auth.log file (Optional)
Once logged in to the server, view the contents of the auth.log file using the cat command as shown.
sudo cat auth.logYou should get output similar to what we have:
Jan 26 09:57:08 ubuntu sshd[255078]: Failed password for root from 138.68.226.175 port 53006 ssh2
Jan 26 09:57:09 ubuntu sshd[255082]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=211.112.187.197 user=root
Jan 26 09:57:09 ubuntu sshd[255078]: error: maximum authentication attempts exceeded for root from 138.68.226.175 port 53006 ssh2 [preauth]
Jan 26 09:57:09 ubuntu sshd[255078]: Disconnecting authenticating user root 138.68.226.175 port 53006: Too many authentication failures [preauth]
Jan 26 09:57:10 ubuntu sshd[255080]: Failed password for root from 38.60.204.121 port 58334 ssh2
Jan 26 09:57:11 ubuntu sshd[255082]: Failed password for root from 211.112.187.197 port 5197 ssh2
Jan 26 09:57:11 ubuntu sshd[255080]: error: maximum authentication attempts exceeded for root from 38.60.204.121 port 58334 ssh2 [preauth]The auth.log log file logs all authentication attempts made to a server. You will see multiple unknown and unauthorized requests being received by your server.
In the next step, we will make changes to the default ssh configuration file.
Step 3. Modifying SSH config file
Before disabling ssh root login make sure you have created a non-root user with sudo access, or should have access to the console. This makes sure you still have access to the system after disabling ssh on root.
The /etc/ssh/sshd_config is the default configuration file for the ssh daemon. It contains all the settings pertaining to the ssh service and handles all SSH connections.
Using your favorite text editor, open the sshd configuration file.
sudo /etc/ssh/sshd_configNavigate and locate the PermitRootLogin line. Change the value from yes to no to block remote root access.
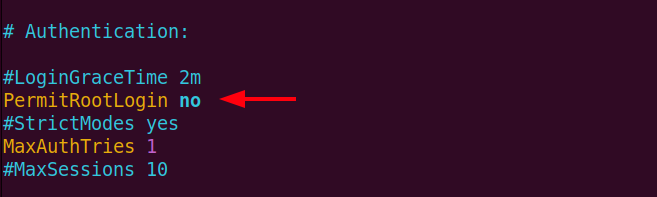
Save the changes and close the file.
Remember editing PermitRootLogin value to no will completely disable ssh root login including SSH key-based login. Whereas setting PermitRootLogin to prohibit-password will disable root password login and at the same time allows ssh key-based login.
Step 4. Restart sshd service
To apply the changes, restart SSH using the following command. Restarting updates the ssh configuration and effects the changes made.
sudo systemctl start sshdStep 5. Verifying SSH Root Login
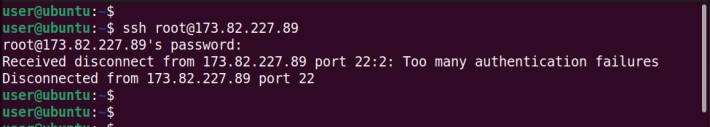
To confirm that root login via SSH has been disabled, access your terminal window and try logging in as root user.
ssh root@your_server_ipIf you are using the SSH key, the command will appear as shown.
ssh -i your_private_key root@your_server_ipIn both cases, you will get an authentication error confirming that root login has been disabled.
Conclusion
In this guide, we have demonstrated how to disable remote root login using the SSH protocol.
Logging as a regular user, and running commands, for that matter, is the best practice when accessing and administering a Linux system. It helps to mitigate any security risks resulting from brute force attacks and keeps your system safe.




Comments